Open Source Intelligence Gathering Using Google Hacking Database
When you think of hacking, the first thing that comes to your mind is probably someone wearing a Guy Fawkes mask and black hand gloves (Trust me, I can't wrap my head around the need for the gloves either), hunched over a computer, and tapping away at it fervently. But, do you know that the regular google we all know can be a hacking tool?
To understand how this works, first, we have to know the basics of something called search query parameters. Search query parameters are specific inputs we add to search keywords to specify what exactly we want. For example, the inurl parameter followed by a colon ':' would make all the URLs that appear in the search result contain the keyword I specified.
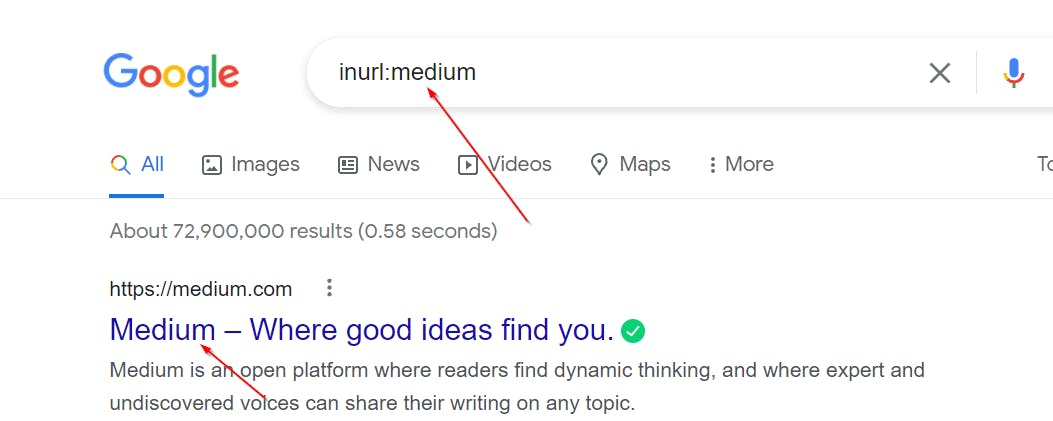
Here, I use the word 'medium'. Try this, and you would see that all the links have 'medium' in them. Other interesting parameters exist such as filetype, intext, insite.
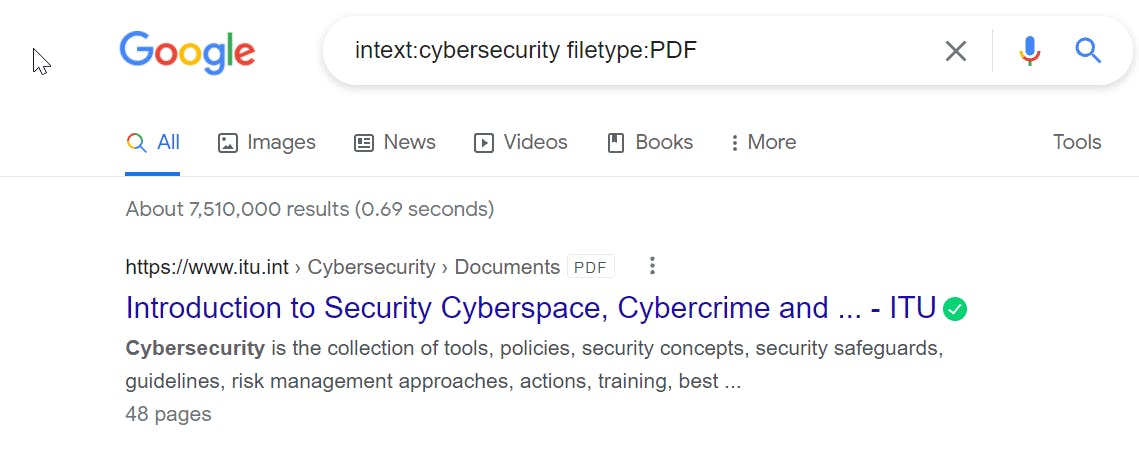
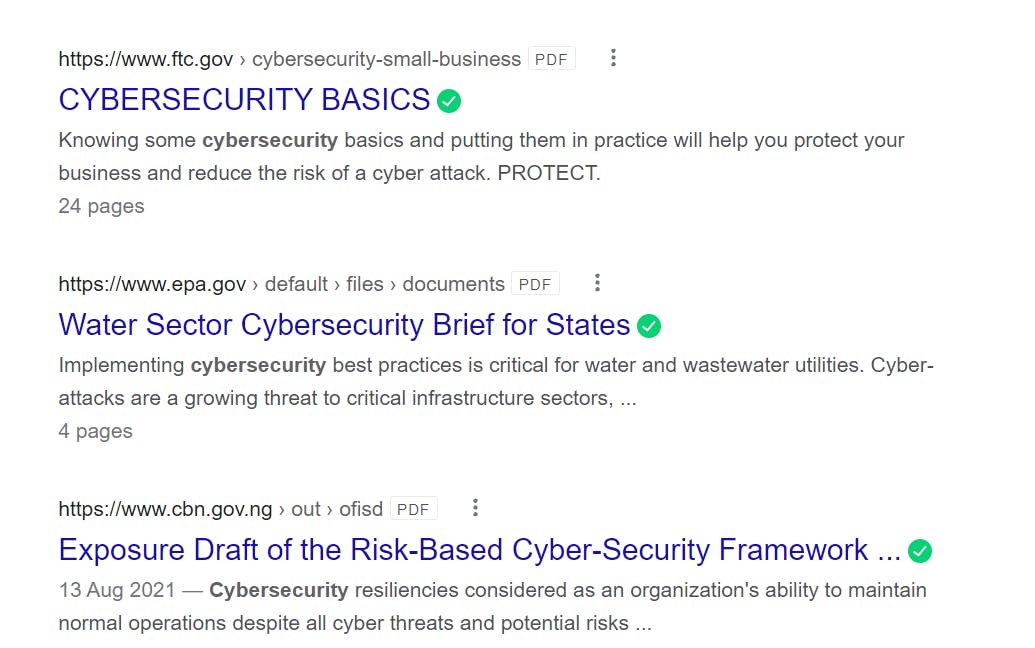
The filetype parameter which I set to PDF will limit my search results to PDF files only. As you can observe too, the results all have 'cybersecurity in the body of the text.
These are only a few of the search query parameters. Over time, more people began creating more parameters, putting them together, and generating shocking results. The queries led to the discovery of vulnerable webcams, servers, exposed databases containing users' names and passwords, etcetera. every day, new things are discovered and they are stored in a repository of common vulnerabilities and exploits known as the google hacking database. You can access them through this website: exploit-db.com
So here is an example of how to use the database. If I wanted to discover vulnerable webcams all I have to do is search webcams in the search bar.
C:\Users\Erere Onyeugbo\Pictures\ghdb explopit db.png
Notice that all results have some of the query parameters we discussed embedded in them. The next step is to click on any one of those links and voila, you will be able to access vulnerable webcams. it is necessary to note that most of the webcams there are yawcams and window XP cameras as they are highly vulnerable. When making use of these tools, stick to passive reconnaissance. this means that you should not actively try to crack the passwords of admin login pages or perform any malicious activities. the google backing database is just the tip of the iceberg of what Open Source Intelligence gathering. Other tools include my favorite- Shodan, Maltego, spiderfoot, the harvester on Kali Linux, grep.app, intelligence X, etc.
Be sure to check out most of these tools to begin your ethical hacking journey.